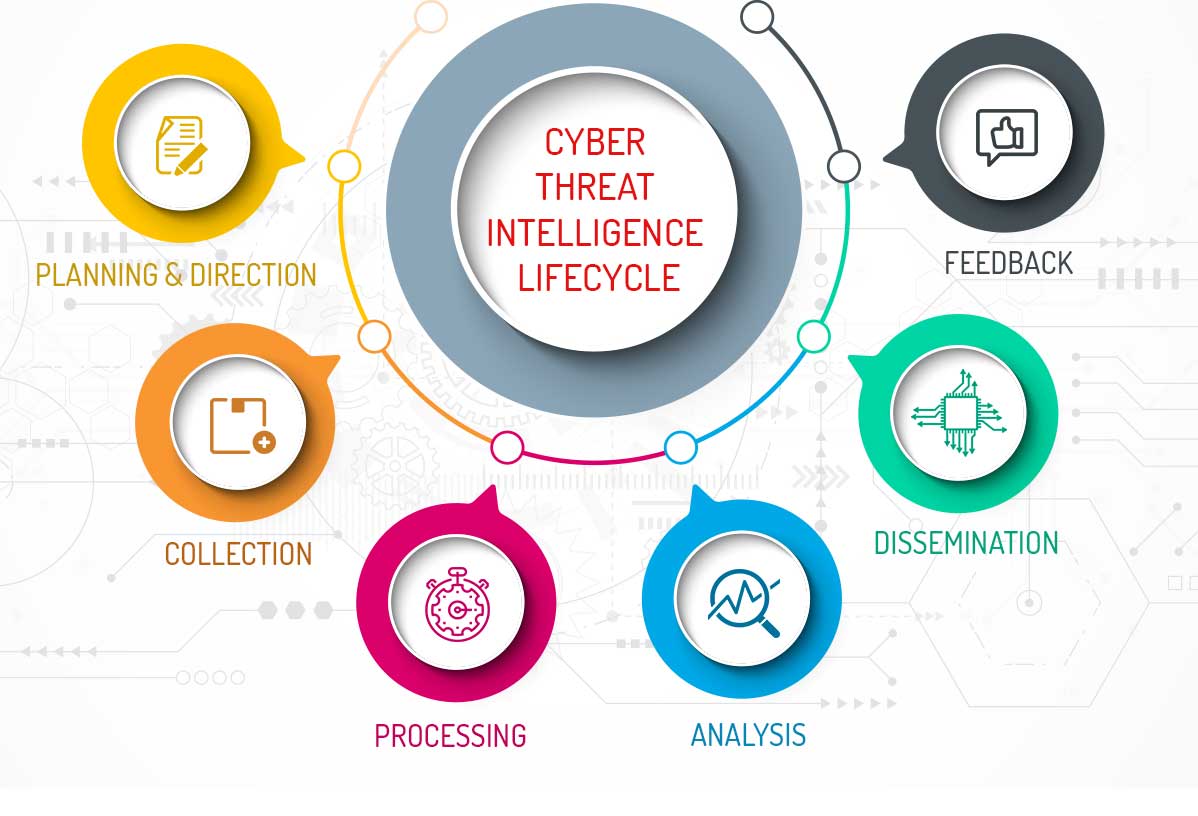
Faced with an overwhelming threatscape and vast numbers of new threat intelligence products and services to consider, staying ahead of potential attacks specific to your company and mission is daunting. The increasing volume and speed of dynamic and emerging threats has left organizations scrambling to effectively respond. By incorporating cyber threat intelligence into their security operations, leading organizations can shorten the time to detection of relevant threats and respond more effectively.
Cytex’s Cyber Threat Intelligence services engage with your key stakeholders to develop or mature your organization’s actionable threat intelligence program. We enhance your security operations by helping you define an organization-specific cyber threat landscape tailored to your unique business environment. Our expert team assesses, develops and matures information collected by native and peripheral sources, allowing you to take immediate action.
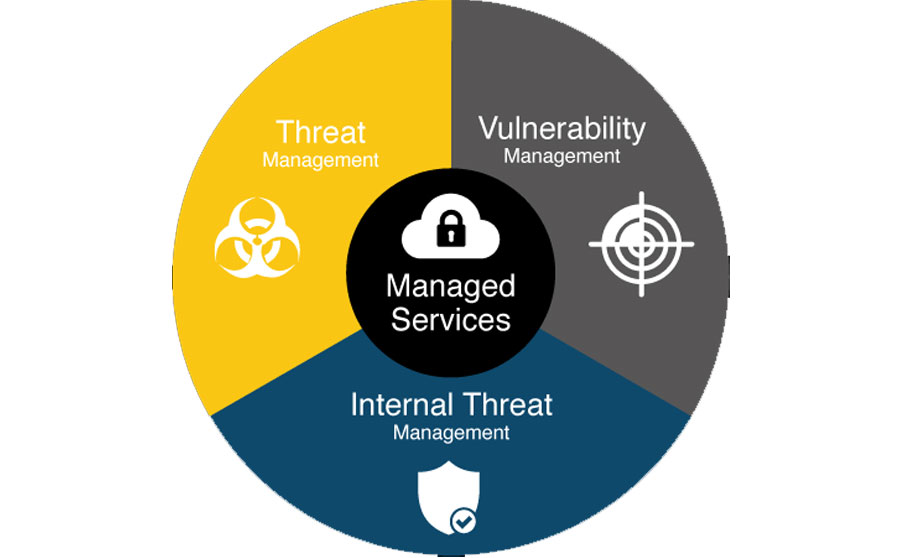
we can alleviate the time and experience needed to manage your endpoint solutions.
Read More
Delivered out of our state of the art SOC, we provide 24x7x365 support, monitoring and real-time recommendations.
Read More
Delivered out of our state of the art SOC, we provide 24x7x365 support, monitoring and real-time recommendations.
Read More